
Evaluating Cybersecurity Preparedness at Asset Managers – Part One
Here, we evaluate cybersecurity preparedness, highlighting some of the key prevention measures we look for in asset managers in today’s environment.
Past performance is not necessarily indicative of future results. No assurance can be given that any investment will achieve its given objectives or avoid losses. Unless apparent from context, all statements herein represent GCM Grosvenor’s opinion.
The number of cyber-attacks and phishing attempts continue to rise across every industry globally, and the asset management industry is not immune. For investors, analyzing cybersecurity risks and the preparedness of asset managers has become a critical part of the due diligence process.
In developing a comprehensive cybersecurity program, we believe that asset managers should view cybersecurity incidents as a “when, not if” problem. While incidents are not guaranteed to occur, it is our view that asset managers should be adequately prepared to defend against potential threats and thus must invest sufficient resources into comprehensive information- and cyber-security programs. This is not limited solely to hardware and software solutions, but also employee cybersecurity training and incident response plans, inclusive of strong mitigation protocols.
As part of our evaluation of managers both pre- and post-investment, we view cybersecurity risk preparedness in two categories: prevention – an asset manager’s commitment to defensive practices – and attack readiness and mitigation – its ability to respond to an attack quickly and effectively. Here, we discuss the first category, highlighting some of the key prevention measures we look for in asset managers in today’s environment.
Cyberattacks on businesses were escalating pre-pandemic and the number of internet crime complaints surged by approximately 70% in 2020, while reported losses exceeded $4.2 billion, a 20% increase.[1] During the abrupt shift to remote work, employees lost the network protection and stability of a corporately managed environment. This shift in day-to-day operations has corresponded with broader trends that have escalated businesses’ susceptibility to cyberattacks.
The movement toward Software-as-a-Service (SaaS) and Platform-as-a-Service (PaaS) solutions, and the adoption of cloud platforms and web-based software have led to increased “outsourcing” of data ownership, and thus potentially less-controlled and less-visible data ownership risk profiles. In addition, businesses are operating in an environment of escalating dissemination of misinformation driven by an uncertain geopolitical landscape. Threat actors are global, and geopolitical changes or uncertainty can lead to increased cyber activity driven by nation-state funded or criminal cyber programs.
Among executives at middle-market firms…
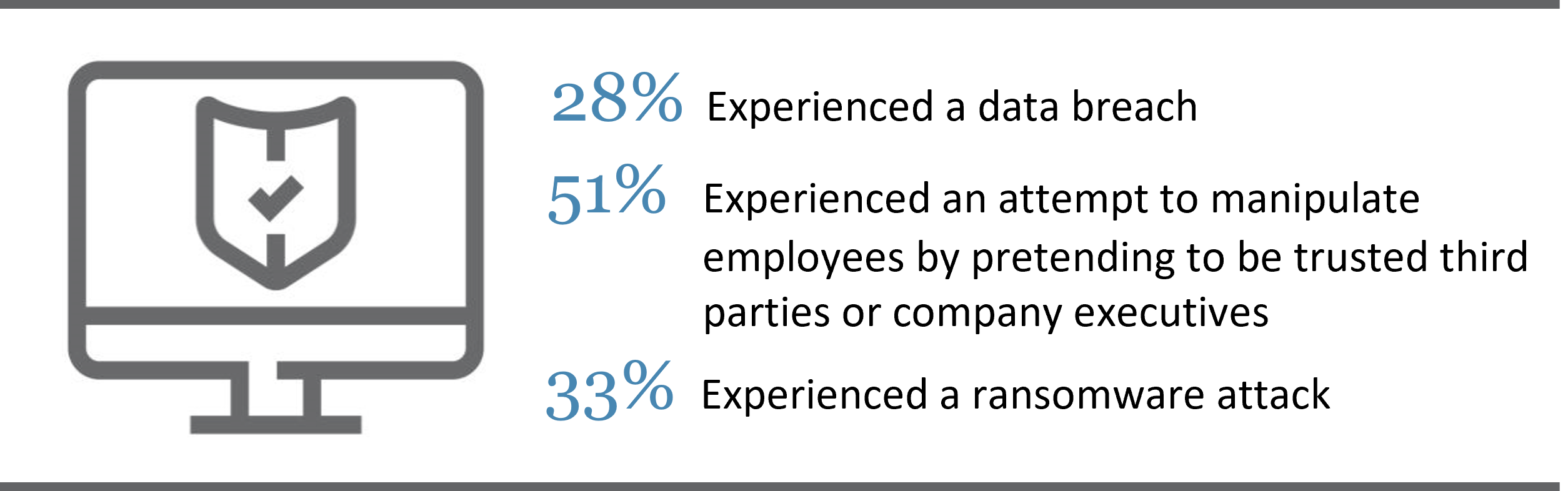
Source: RSM US Middle Market Business Index Cybersecurity Special Report 2021.
Cyberattacks pose a unique risk for asset managers, given their valuable client information, proprietary operational data, and frequent money transfers and transactions. While all companies face some reputational loss after a cyberattack, asset management businesses exist on a critical structure of trust, which can erode substantially in the aftermath of a cyber event.
Reputational issues are especially acute for alternative asset managers, who often aim to avoid publicity. Certain managers, such as hedge funds with an active trading strategy, may be more susceptible to trading losses from denial-of-service attacks due to a system/network outage. In theory, asset managers may be targeted because they likely have both the financial ability to pay ransoms and a high incentive to end a successful cyberattack to keep the incident out of the headlines.
In addition, firms may face severe financial penalties and onerous consumer protection requirements with various regulators as the result of cybersecurity incidents.
At GCM Grosvenor, many of our own cybersecurity controls and processes are based on the NIST Cybersecurity Framework and a Zero Trust architecture (see sidebar), and we apply the same framework when performing diligence on managers with whom we invest.
Because preventative measures need to be customized to protect the unique operations of each firm, we also assess whether the firm has the resources and knowledge (internally or externally) to implement proper cybersecurity controls in a way that’s appropriate for their business.
Some of the security controls and practices we look for in managers include, but are not limited to:
Leading causes of ransomware attacks reported by managed service providers in 2020
Source: Statista. https://www.statista.com/chart/25247/most-common-causes-of-ransomware-attacks/

The rapid adoption of remote work has caused the cybersecurity landscape to evolve in such a sophisticated way that we believe firms should adopt a “Zero Trust” architecture.
Zero Trust, according to the National Institute of Standards and Technology (NIST), is defined as “an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.”
In our view, a Zero Trust approach, combined with a layered defense strategy, is an effective way to protect against cyberattacks.
We believe that implementing the right mix of preventative technologies from among the above is a prerequisite for asset managers seeking to attract institutional capital in today’s market. But we also believe that managers must adopt the right mix of policies and procedures to support technology solutions.
Over the years, we have seen managers stress employee training and policy requirements that seek to promote a culture of good employee behavior, while others may leverage cyber security consultants to perform these functions and add additional layers of protection. Whatever the approach, our view is that the best-prepared firms apply multiple preventative measures.
In part 2 of “Evaluating Cybersecurity Preparedness at Asset Managers,” we will explore the second category of preparedness – readiness and mitigation – and highlight best practices in this area among investment managers.
Learn more about GCM Grosvenor’s operational due diligence capabilities here.

Here, we evaluate cybersecurity preparedness, highlighting some of the key prevention measures we look for in asset managers in today’s environment.
We explore some challenges and unforeseen benefits of performing remote due diligence, and discuss what we believe makes a well-resourced, sophisticated investor properly positioned to conduct due diligence in this environment.
Important Disclosures
For illustrative and discussion purposes only.
No assurance can be given that any investment will achieve its objectives or avoid losses. Past performance is not necessarily indicative of future results.
The information and opinions expressed are as of the date set forth therein and may not be updated to reflect new information.
Investments in alternatives are speculative and involve substantial risk, including strategy risks, manager risks, market risks, and structural/operational risks, and may result in the possible loss of your entire investment. The views expressed are for informational purposes only and are not intended to serve as a forecast, a guarantee of future results, investment recommendations, or an offer to buy or sell securities by GCM Grosvenor. All expressions of opinion are subject to change without notice in reaction to shifting market, economic, or political conditions. The investment strategies mentioned are not personalized to your financial circumstances or investment objectives, and differences in account size, the timing of transactions, and market conditions prevailing at the time of investment may lead to different results. Certain information included herein may have been provided by parties not affiliated with GCM Grosvenor. GCM Grosvenor has not independently verified such information and makes no representation or warranty as to its accuracy or completeness.
Data sources:
[1] Source: FBI Internet Crime Complaint Center 2020 Internet Crime Report. https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf
We offer clients a broad range of tailored solutions across strategies, including multi-strategy, macro, relative value, long/short equity, quantitative strategies, and opportunistic credit. Levaraging our large scale and presence in the industry, we are able to offer clients preferntial exposure to hard-to-access managers and seek to obtain terms that can drive economic and structural advantages.