
Evaluating Cybersecurity Preparedness at Asset Managers – Part One
Here, we evaluate cybersecurity preparedness, highlighting some of the key prevention measures we look for in asset managers in today’s environment.
Past performance is not necessarily indicative of future results. No assurance can be given that any investment will achieve its given objectives or avoid losses. Unless apparent from context, all statements herein represent GCM Grosvenor’s opinion.
In the first installment of “Evaluating Cybersecurity Preparedness at Asset Managers,” we highlighted some proactive and preventative measures that asset managers can take to best prepare for cybersecurity risks. Here we will discuss another component of a well-designed cybersecurity framework: readiness and mitigation – steps that help to effectively respond to a cyberattack and mitigate potential impact and/or losses.
As an investor on behalf of our clients, we consider it part of our fiduciary duty to ensure a high degree of protection of our clients’ data and personal information. Thus, the evaluation of the technology infrastructure and related controls at asset managers with whom we invest has been part of our operational due diligence (ODD) process since the early 2000’s. The risks and threats evolve over time, yet we remain focused. Given the recent surge in cybercrime activities and heightened sensitivity among financial institutions, particularly alternative asset managers, evaluating a firm’s protocols to recognize and react to an incident is as important a focus of our evaluation as it has even been.
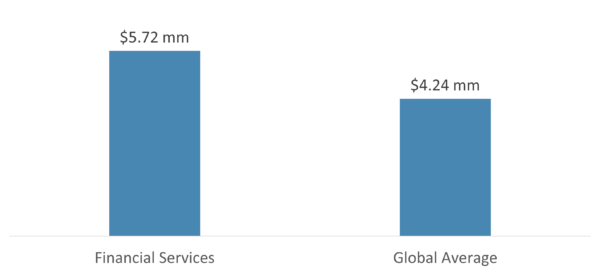
According to one recent study, 70% of financial institutions reported a cyberattack in 2020, an increase of approximately 20% from 2019.[1] And the cost of data breaches is higher in financial services than in other sectors.
We have found that the best-prepared firms are those who have made cyberattack readiness an integral part of their information security program. When evaluating the cyberattack readiness of asset managers, we look for the implementation of certain key practices:
An organization’s response must be instantaneous
When a cyberattack occurs, every moment matters. Well-prepared managers have an incident response plan that details, among other things, who will be responsible in the event of a cybersecurity incident and what actions need to be taken to contain the incident.
An asset manager’s incident response plan should include procedural documentation that is prescriptive in outlining response action steps and should be testable to ensure readiness. Such a plan should be reviewed annually, at a minimum.
Rehearsal of an incident response plan is key
An asset manager should conduct targeted rehearsal exercises to ensure that all those involved understand their responsibilities and are prepared to execute those responsibilities in the event of an attack. It is important to rehearse relevant threat situations (e.g., ransomware attack, Denial of Service (DoS) attack, data breach, etc.) to prepare the organization and those responsible for reacting to real life threats.
Diversification and redundancy should be part of a data storage solution
Data backups are an essential form of self-insurance. An organization should understand what data it has, how and where it is stored, and determine the appropriate data backup and restoration protocols. If these areas are addressed properly, the threat of data and financial loss from a cybersecurity incident poses a much lower risk of disrupting the business. Importantly, an asset manager must test these protocols to ensure reliability of the data storage and the restoration speed required amongst its critical and non-critical systems. Mature incident response programs will have target Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) which dictate how data is backed up and restored.
When done effectively, a manager can mitigate the potential loss from an incident and more quickly recover its operational environment.
The right personnel and resources are capable of containing a cyberattack
We assess the skillset of an asset manager’s cyberattack response resources; an asset manager should have the proper resources to adequately manage and oversee its information security environment based on the size and complexity of its business. Whether an asset manager has dedicated in-house cybersecurity personnel, engagements with external response mitigation teams, or both, it is important for the roles and responsibilities to be documented and understood by all parties involved. For many asset managers, especially small and emerging managers, suitable cybersecurity resources can be provided through an external consultant. Additionally, many firms have also engaged an external incident response mitigation team, who can be ready 24/7 should an unexpected issue arise.
A growing number of companies are insuring against disruption to their operations
Some firms are required to obtain insurance to cover business interruption from a regulatory perspective, while others are doing so voluntarily as it is becoming a sound business practice among larger asset managers. While cyber insurance cannot mitigate reputational losses, it can help to backstop financial losses arising from an attack. The cyber insurance market is evolving and growing; at insurance broker Marsh McLennan, the number of companies who have added cyber insurance has nearly doubled in four years.
Percent of eligible companies who have added coverage
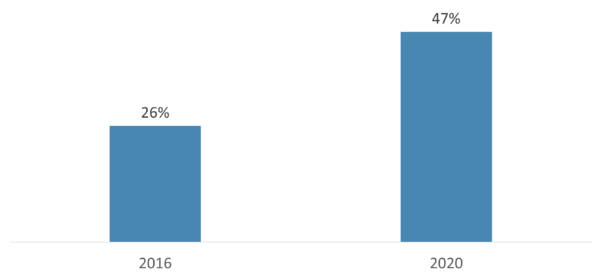
At this stage, we recommend firms closely evaluate their cybersecurity risk profile, including relevant information technology hardware, to ensure proper coverage for the specific risks each asset manager may face.
We believe focusing on, and implementing, these elements are crucial to a firm’s ability to mitigate potential damages arising from a cyber incident. Asset managers must take a tailored approach to cyber defense, and our ODD team evaluates whether an asset manager’s overall technology program is appropriate for the size and strategy of the business, including any regulatory requirements. We feel that this “right-sizing” review, along with an evaluation of the individual(s) responsible for implementation of an asset manager’s cyber program, is important to assessing cyber defense and can often be overlooked.
Regardless of the size and strategy at an asset manager, GCM Grosvenor looks for strong enterprise protocols, shares our insights with managers to ensure best practices, and ultimately requires an asset manager’s cyber security program to meet our underwriting standards.
Learn more about GCM Grosvenor’s operational due diligence capabilities here.

Here, we evaluate cybersecurity preparedness, highlighting some of the key prevention measures we look for in asset managers in today’s environment.
We explore some challenges and unforeseen benefits of performing remote due diligence, and discuss what we believe makes a well-resourced, sophisticated investor properly positioned to conduct due diligence in this environment.
Important Disclosures
For illustrative and discussion purposes only.
No assurance can be given that any investment will achieve its objectives or avoid losses. Past performance is not necessarily indicative of future results.
The information and opinions expressed are as of the date set forth therein and may not be updated to reflect new information.
Investments in alternatives are speculative and involve substantial risk, including strategy risks, manager risks, market risks, and structural/operational risks, and may result in the possible loss of your entire investment. The views expressed are for informational purposes only and are not intended to serve as a forecast, a guarantee of future results, investment recommendations, or an offer to buy or sell securities by GCM Grosvenor. All expressions of opinion are subject to change without notice in reaction to shifting market, economic, or political conditions. The investment strategies mentioned are not personalized to your financial circumstances or investment objectives, and differences in account size, the timing of transactions, and market conditions prevailing at the time of investment may lead to different results. Certain information included herein may have been provided by parties not affiliated with GCM Grosvenor. GCM Grosvenor has not independently verified such information and makes no representation or warranty as to its accuracy or completeness.
Data sources:
[1] Source: “Cybercriminals Cash Out as Finance Industry Becomes Lucrative Target,” Keeper Security, Inc., January 27, 2021, https://www.keeper.io/hubfs/press/Ponemon_Finance_PressRelease2021.pdf
[2] Source: “Cost of a Data Breach Report 2021,” IBM, https://www.ibm.com/security/data-breach
[3] Source: “Ransomware claims are roiling an entire segment of the insurance industry,” The Washington Post, June 17, 2021, https://www.washingtonpost.com/technology/2021/06/17/ransomware-axa-insurance-attacks/
GCM Investments UK LLP (GCMUK) has been made aware of fraudulent schemes targeting members of the public in the United Kingdom.
Unauthorised individuals are falsely claiming to represent GCMUK and are misusing the firm’s name and publicly available information in connection with fake investment opportunities.
These scams are sophisticated and deliberately misleading. They may involve the use of real GCMUK employee names and may imitate the tone, format, and branding of genuine GCMUK communications.
Please note:
GCMUK does not offer financial services or products to retail clients, either directly or through third parties. You can verify GCMUK’s regulatory status and permissions on the Financial Conduct Authority (FCA) Register at register.fca.org.uk.
If you are based in the UK and believe you have been contacted by a fraudster claiming to represent GCMUK, please take the following steps:
Investor Scam Alert
GCM Grosvenor L.P. and its affiliated entities (collectively, “GCMG”) have been made aware of fraudulent schemes currently targeting members of the public in Malaysia and Hong Kong, in which unauthorised individuals are falsely claiming to represent GCMG in connection with purported investment opportunities.
These fraudulent individuals are believed to be actively promoting false investment opportunities, often involving mobile applications, through the unauthorised use of GCMG’s name, brand, corporate logo, and other identifying materials. We have also received reports that these parties may be distributing fabricated business cards, hosting online webinars, creating WhatsApp groups, and arranging personal video calls to simulate legitimacy. These scams are sophisticated and deliberately misleading, frequently involving the use of real GCMG employee names and imitating the style, tone, and presentation of genuine GCMG communications.
GCMG has no presence, operations, or authorised representatives in Malaysia. GCMG does not offer any investment schemes, products, or mobile applications targeted at Malaysian investors, either directly or indirectly.
While GCMG maintains a legitimate presence and employs personnel in Hong Kong, these scams are entirely unauthorised and unrelated to any genuine activities conducted by GCMG or its employees in the region.
Position of GCMG
GCMG has neither authorised nor endorsed any such solicitations and takes this matter seriously. We have reported some of these incidents to the relevant regulatory and enforcement authorities in Malaysia, and are doing the same in Hong Kong, including notifying the Hong Kong Police and the appropriate financial regulators. GCMG will continue to assist with their investigations.
GCMG is actively monitoring these developments and reserves all rights to take legal action against any party found misusing its name, brand, or intellectual property.
While these reports currently centre on activity in Malaysia and Hong Kong, the methods used may be replicated in other jurisdictions. GCMG continues to monitor for similar risks globally.
Unauthorized individuals are impersonating Winston Chow in scams targeting investors, particularly in Malaysia. He does not solicit investments directly in Asia. If you are contacted by someone claiming to be him outside of official channels, please report it to local authorities.
For verification or further information, please contact: [email protected]
Investor Scam Alert
Unauthorized individuals are impersonating Winston Chow in scams targeting investors, particularly in Malaysia. He does not solicit investments directly in Asia. If you are contacted by someone claiming to be him outside of official channels, please report it to local authorities.
For verification or further information, please contact: [email protected]
We offer clients a broad range of tailored solutions across strategies, including multi-strategy, macro, relative value, long/short equity, quantitative strategies, and opportunistic credit. Levaraging our large scale and presence in the industry, we are able to offer clients preferntial exposure to hard-to-access managers and seek to obtain terms that can drive economic and structural advantages.